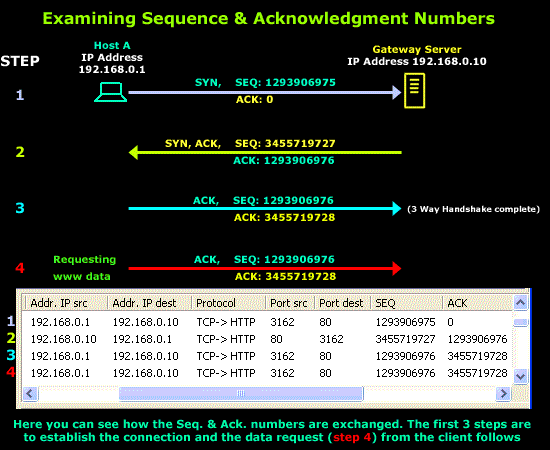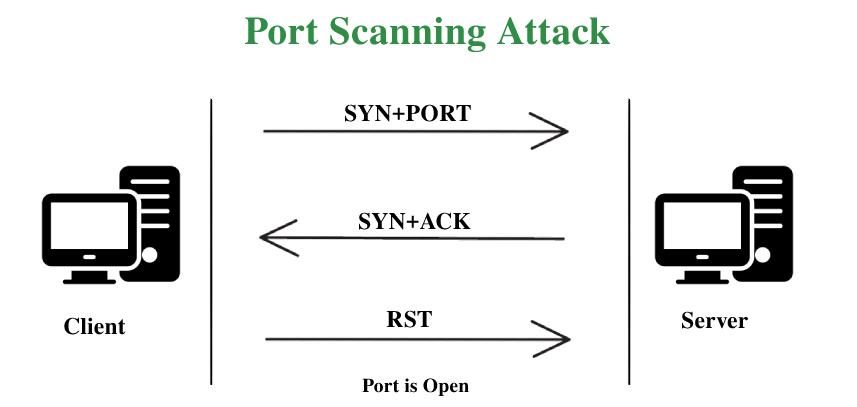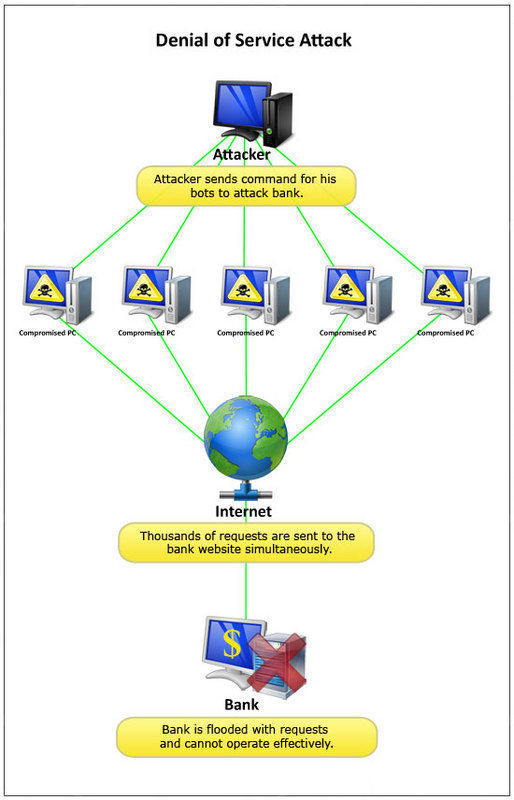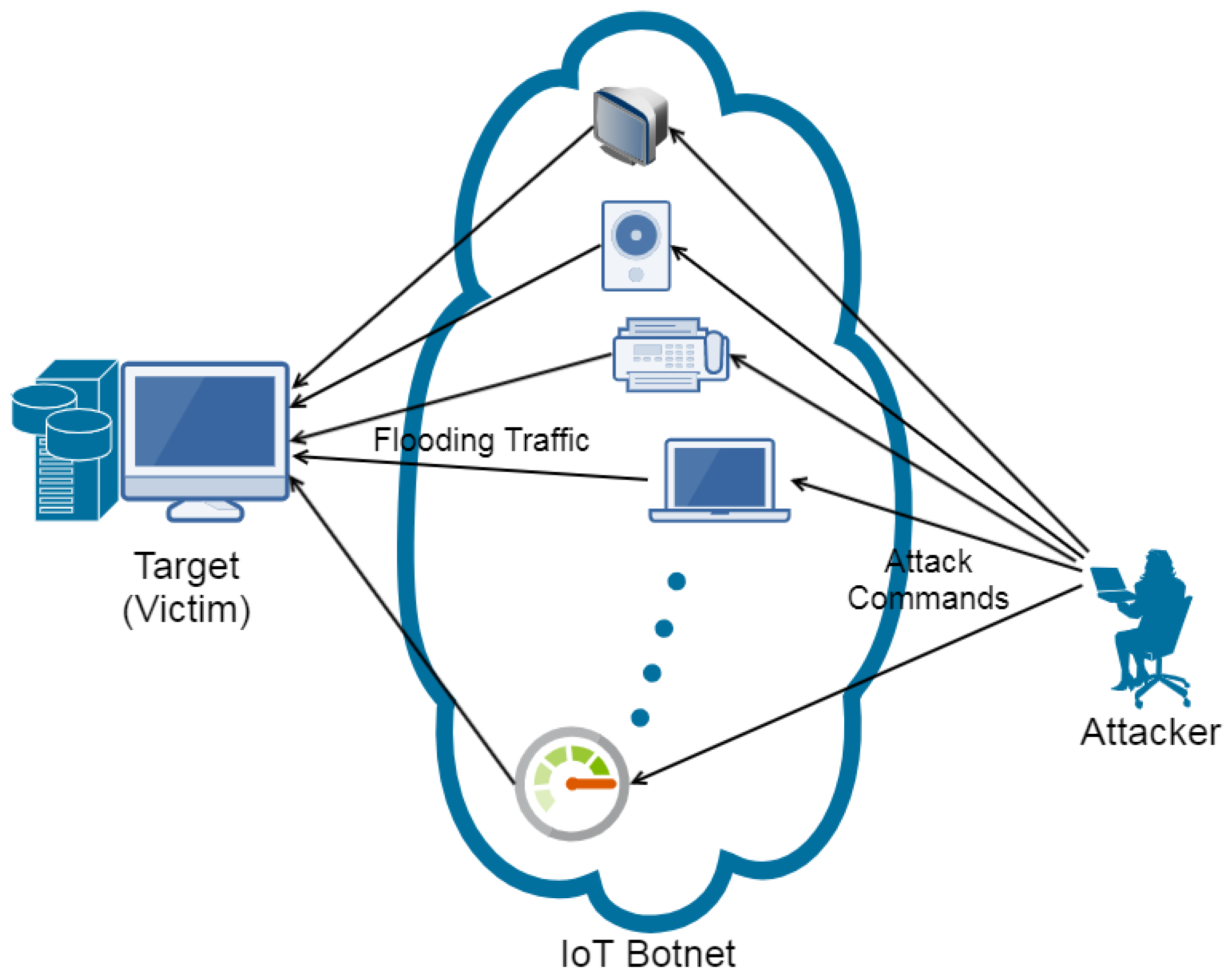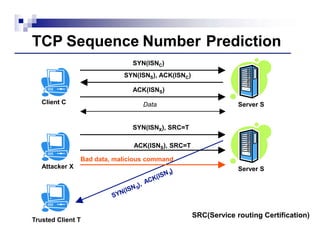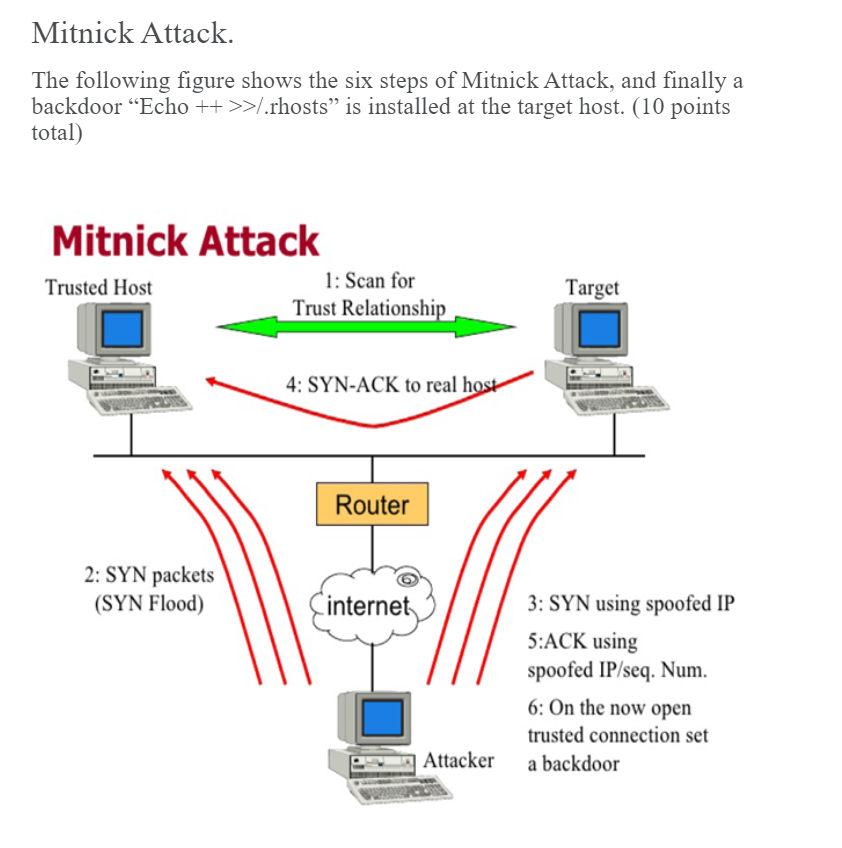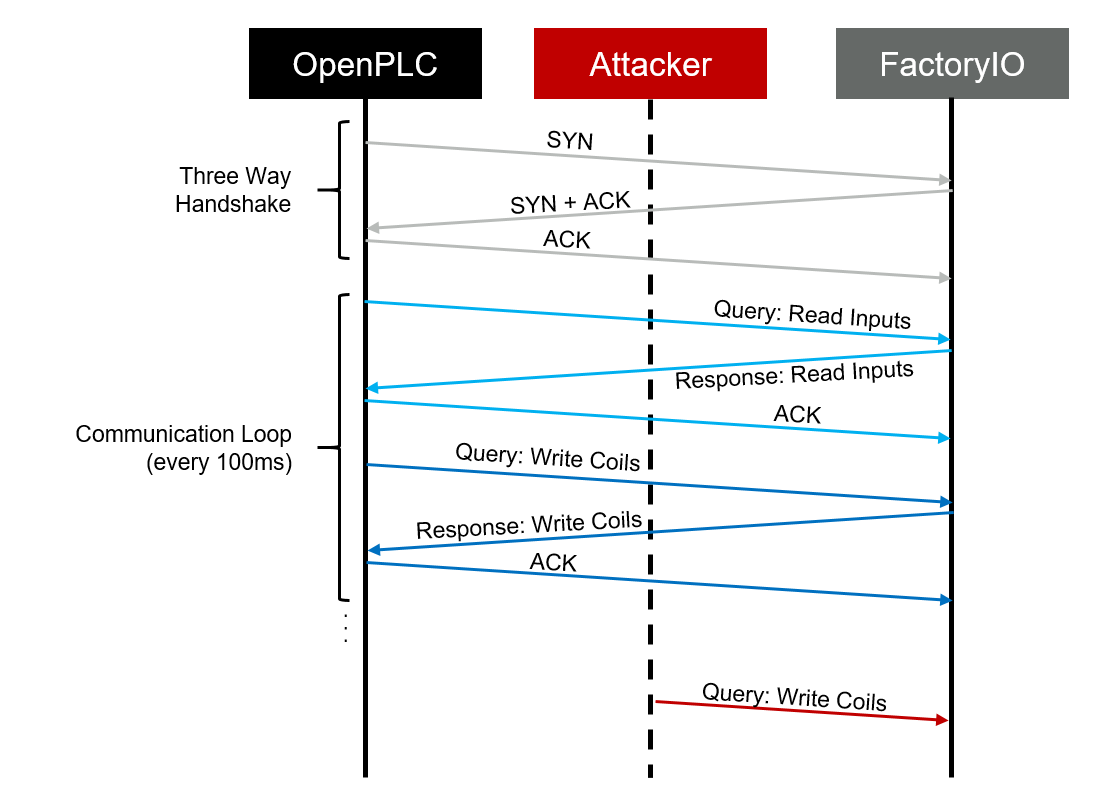
Tcp Sequence Prediction Attack Images, Tcp Sequence Prediction Attack Transparent PNG, Free download

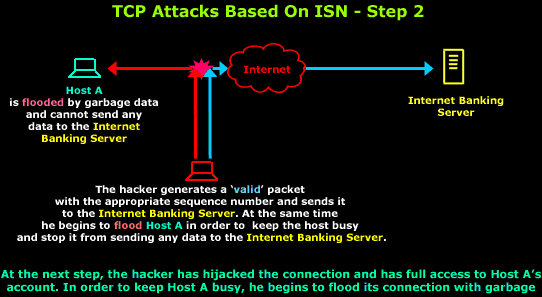
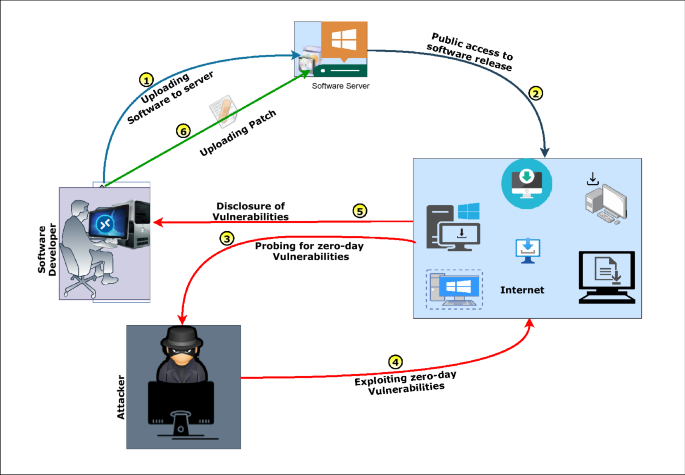
Today In Infosec on Twitter: "1994: Kevin Mitnick allegedly performed a remote attack against Tsutomu Shimomura's personal computer, gaining access by using source address spoofing and TCP sequence prediction. But there's no

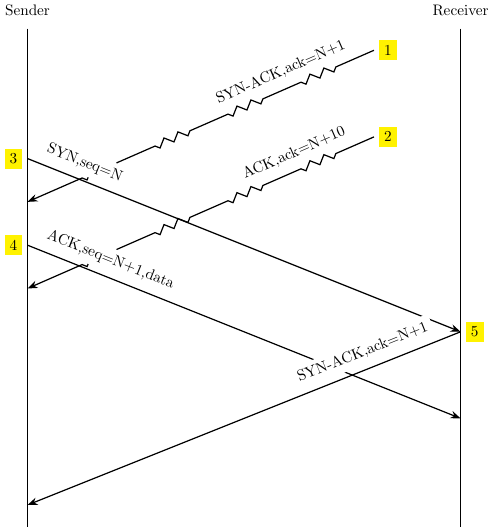
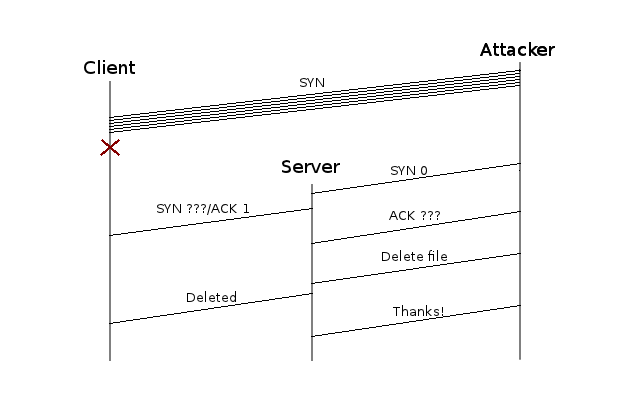
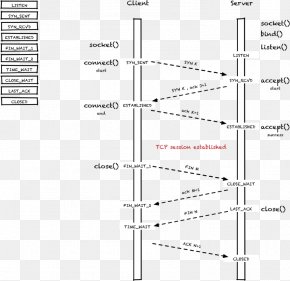
Transmission Control Protocol Sequence Diagram TCP Sequence Prediction Attack OmniGraffle, PNG, 730x708px, Transmission Control Protocol, Acknowledgement,