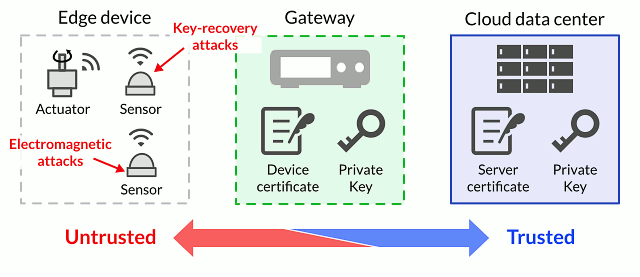
New Security Signals study shows firmware attacks on the rise; here's how Microsoft is working to help eliminate this entire class of threats | Microsoft Security Blog

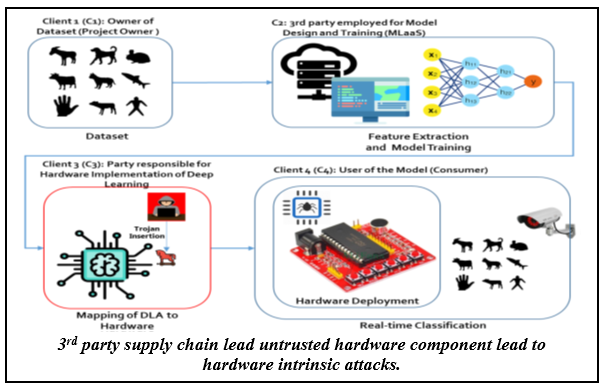
A Review on Hardware Security Countermeasures for IoT: Emerging Mechanisms and Machine Learning Solutions

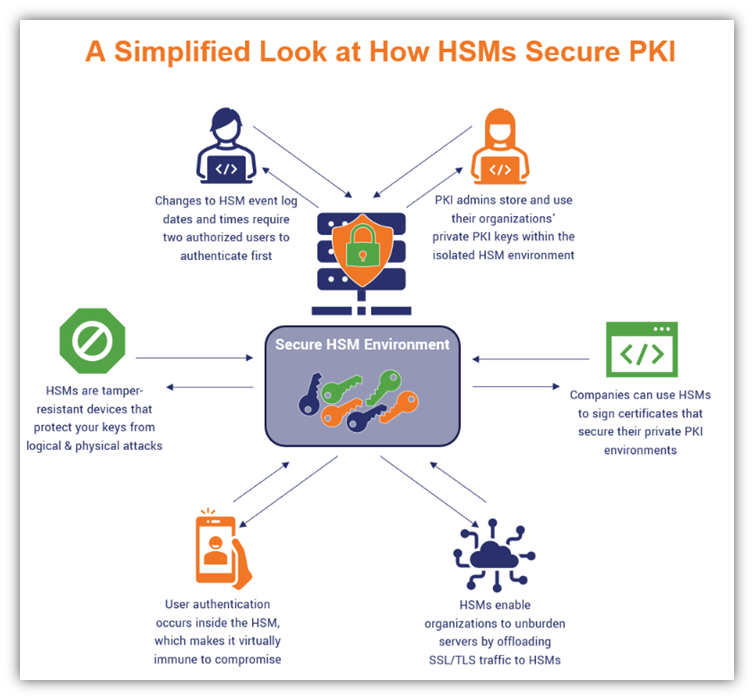
The Hardware Hacking Handbook: Breaking Embedded Security with Hardware Attacks : van Woudenberg, Jasper, O'Flynn, Colin: Amazon.de: Bücher
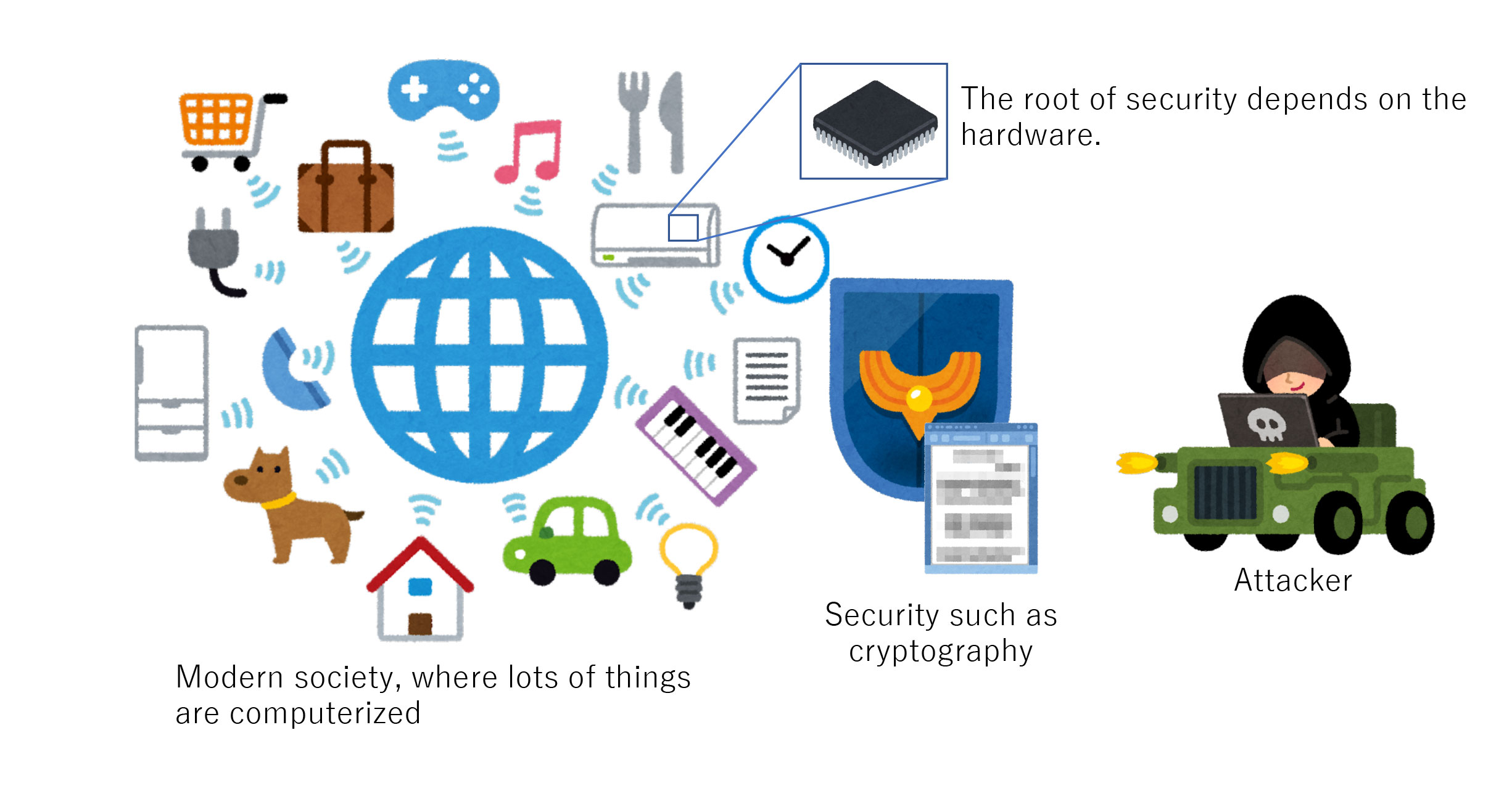






![PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fac9e722cd47fa28222a53bb4d624a42d0d0d04/7-Figure4-1.png)


![PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fac9e722cd47fa28222a53bb4d624a42d0d0d04/5-Figure3-1.png)



![PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fac9e722cd47fa28222a53bb4d624a42d0d0d04/3-Figure2-1.png)